Hawkeye SCS Managed Security Services
Leverage BITCON's security services to address security and compliance needs.
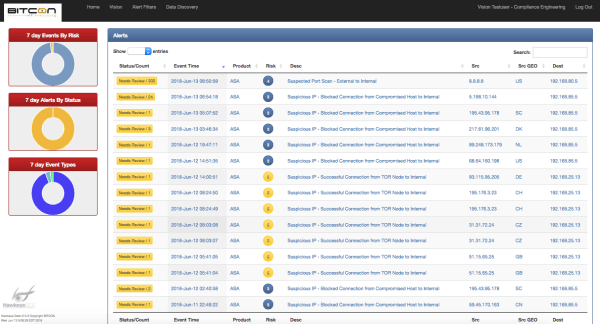
Vision
Vision's real-time threat intelligence feeds provide up to the moment data on suspicious hosts and potential attacks. Unlike traditional SIEM tools where you’re expected to develop rules and reports, BITCON’s team of skilled security engineers have already done the work for you.
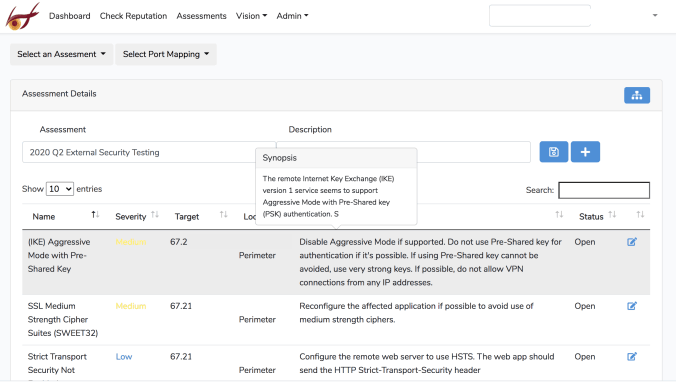
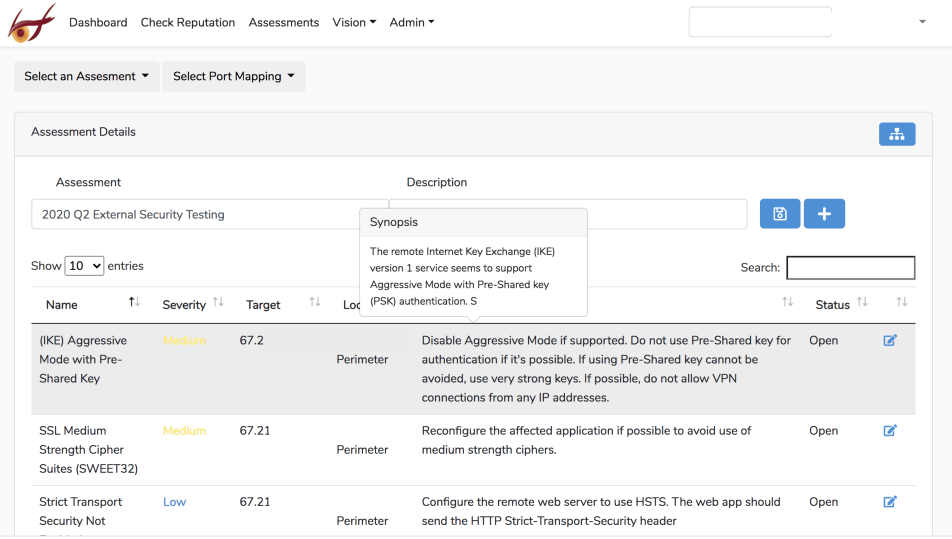
Assessments
Assesments provides visibility into security assessment reporting. Portal access to security testing results assist clients with managing issues so they can anticipate security risks and prevent breaches to critical systems and valuable information.